In a world where data breaches can destroy trust overnight, privacy cannot survive as a checklist exercise. Modern privacy leaders know this truth better than anyone: Compliance keeps you out of trouble, but risk management keeps you in business.
Today’s most resilient organizations do more than follow the rules. Modern privacy leaders build programs that are dynamic, predictive, and fully woven into business strategy. Privacy becomes a catalyst for innovation and a driver of trust in an era where AI, global regulations, and expanding data ecosystems shift as rapidly as a season finale plot twist.
This is your guide to building a privacy program designed not only to keep pace with change but to lead it.
What is privacy risk management?
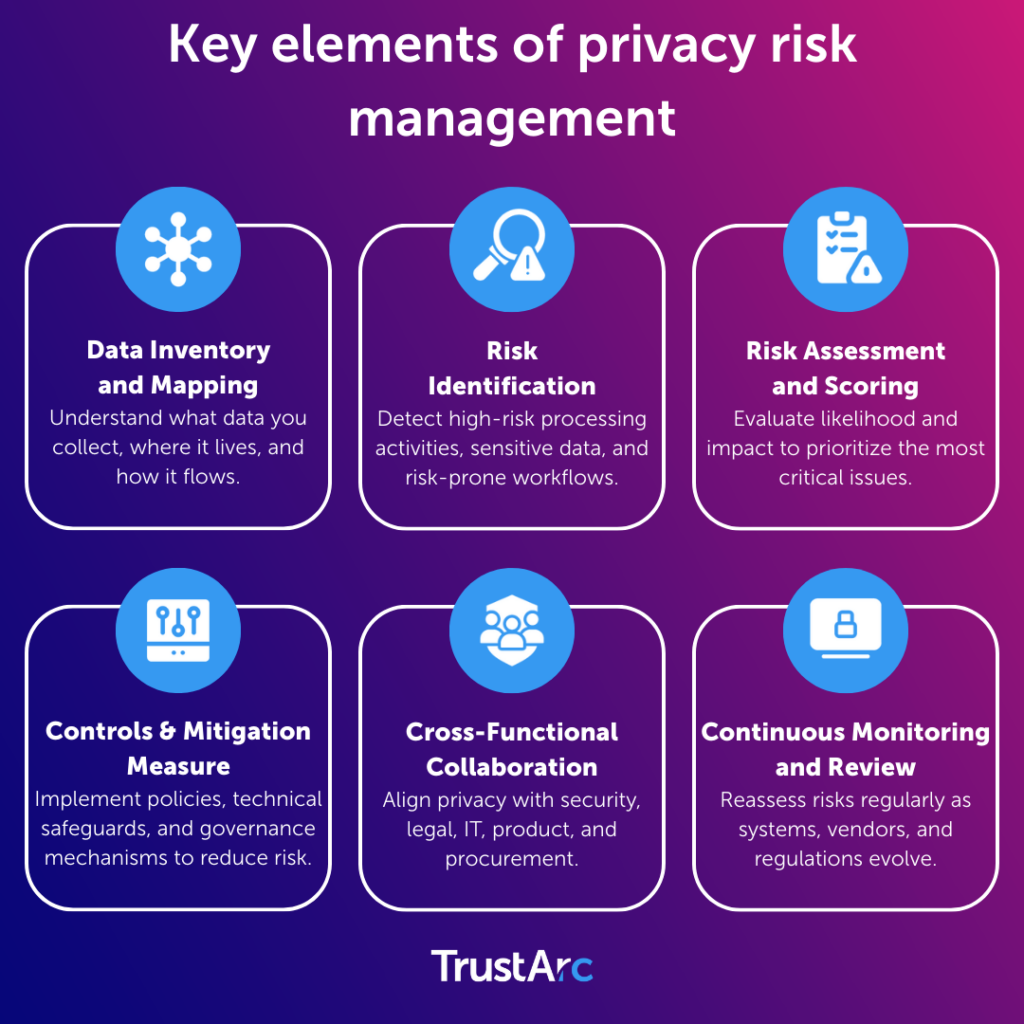
Privacy risk management is a proactive, strategic approach to identifying, assessing, and mitigating data privacy risks across an organization’s operations.
It goes beyond the minimum legal requirements to examine holistically how data practices, systems, vendors, and emerging technologies impact individuals and the business.
Privacy as an enterprise strategy
Forward-thinking organizations weave privacy into their business strategy, not as a compliance obligation, but as a competitive differentiator. When leaders understand their data flows, high-risk processes, and exposure points, they can innovate confidently instead of cautiously.
Risk-based models outperform compliance-only approaches
Risk-based organizations identify problems before regulators do. They align privacy with security, engineering, procurement, HR, and product—creating unified systems that scale, adapt, and protect.
Governance structures thrive on risk thinking
Cross-functional governance committees, privacy champions, and risk scoring frameworks turn privacy from a reactive function into a strategic engine that drives trust, operational resilience, and stronger decision-making.
Discover how TrustArc enables organizations to streamline their privacy risk management through automated vendor assessments and scalable workflows.
Understanding the shift from checkbox compliance
Checkbox compliance is the “just tell me what to do” approach to privacy: follow the rules, fill out the forms, publish the policy, and hope for the best.
It’s not enough anymore.
The limitations of checklist thinking
-
- It’s reactive: You only address what’s required today, ignoring tomorrow’s risks.
- It creates blind spots: Complex data ecosystems, vendors, AI models, and cross-border transfers don’t fit neatly into static checklists.
- It breaks at scale: As regulations multiply, checklists expand until they become unmanageable.
- It frustrates stakeholders: Teams view privacy as bureaucratic rather than strategic.
The real risks of minimal compliance
- Regulatory penalties
- Customer distrust
- Third-party failures
- Security incidents
- Brand and reputational damage that outlives the news cycle
We’ve all watched companies pay the price, whether through preventable breaches, AI rollouts paused after public backlash, or consent violations that made headlines. Many of these organizations checked every required box, yet their programs lacked the depth needed to manage real-world risk.
Why global regulations favor risk-based approaches
From GDPR to the Colorado AI Act to Brazil’s LGPD, regulators are steering organizations toward demonstrable accountability. Risk-based governance is no longer optional; it’s the expectation.
Key differences: Risk management vs. checkbox compliance
| Criterion | Privacy risk management | Checkbox compliance |
|---|---|---|
| Mindset | Proactive | Reactive |
| Focus | Reducing data privacy risks | Meeting minimum legal requirements |
| Tools | DPIAs, risk scoring, data mapping, privacy frameworks | Policies and forms |
| Outcome | Stronger protections, trust, innovation | Gaps, outdated practices, hidden vulnerabilities |
This is the difference between being ready and being surprised.
The role of the risk assessment process in modern privacy programs
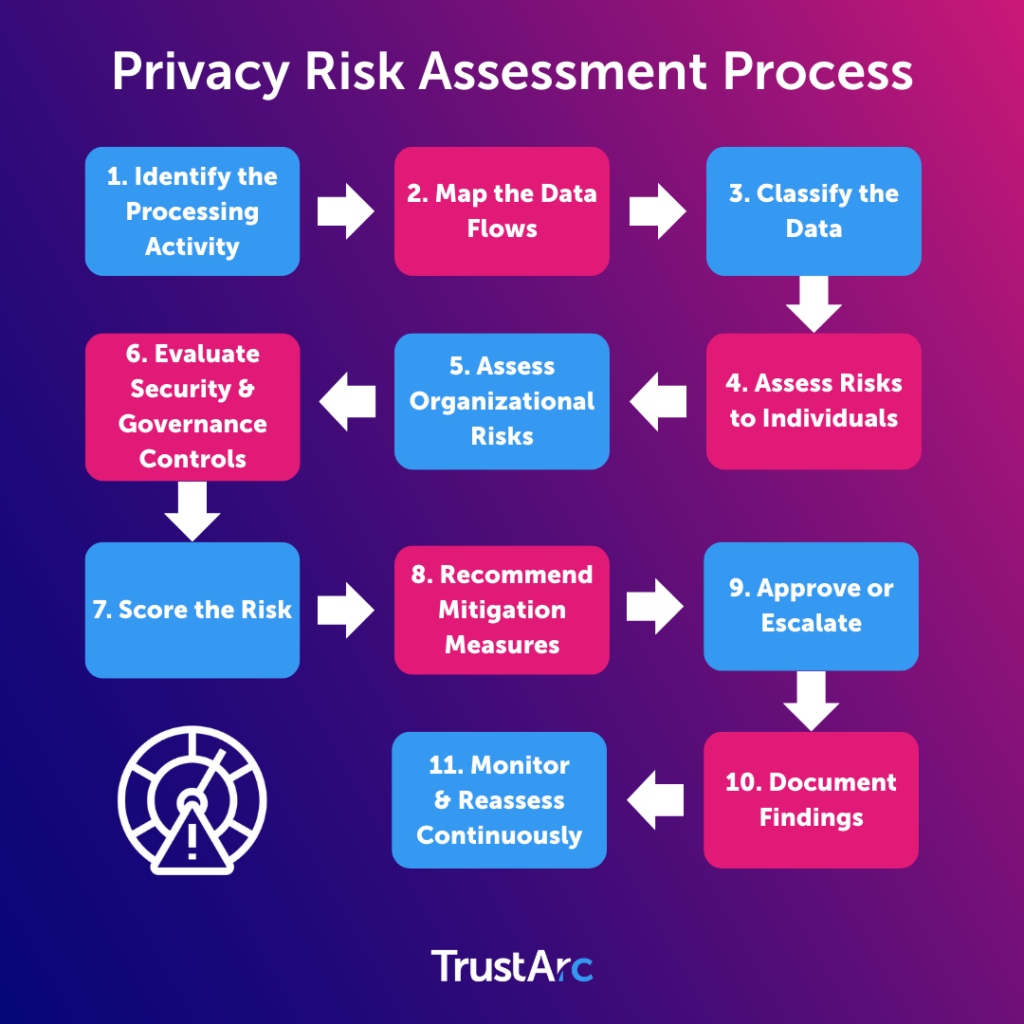
Risk assessments are the beating heart of a modern privacy program. They transform abstract concerns into measurable, actionable, prioritized steps.
What a privacy risk assessment covers
- Nature and purpose of processing
- Data sensitivity and volume
- Individuals affected
- Technology involved
- Likelihood and severity of harm
- Third-party involvement
- Security posture
- Legal and regulatory exposure
Techniques leaders rely on
- Data Protection Impact Assessments (DPIAs)
- Privacy Impact Assessments (PIAs)
- Third-party risk reviews
- Data inventories and mapping
- AI impact, bias, or ethics assessments
Why it outperforms checklist compliance
Risk assessments uncover the “unknown unknowns,” including shadow data, misconfigurations, AI model surprises, vendor gaps, and internal usage that policies no longer reflect.
This is where privacy leaders move from “following the law” to “leading the organization.”
Common data privacy risks organizations must manage
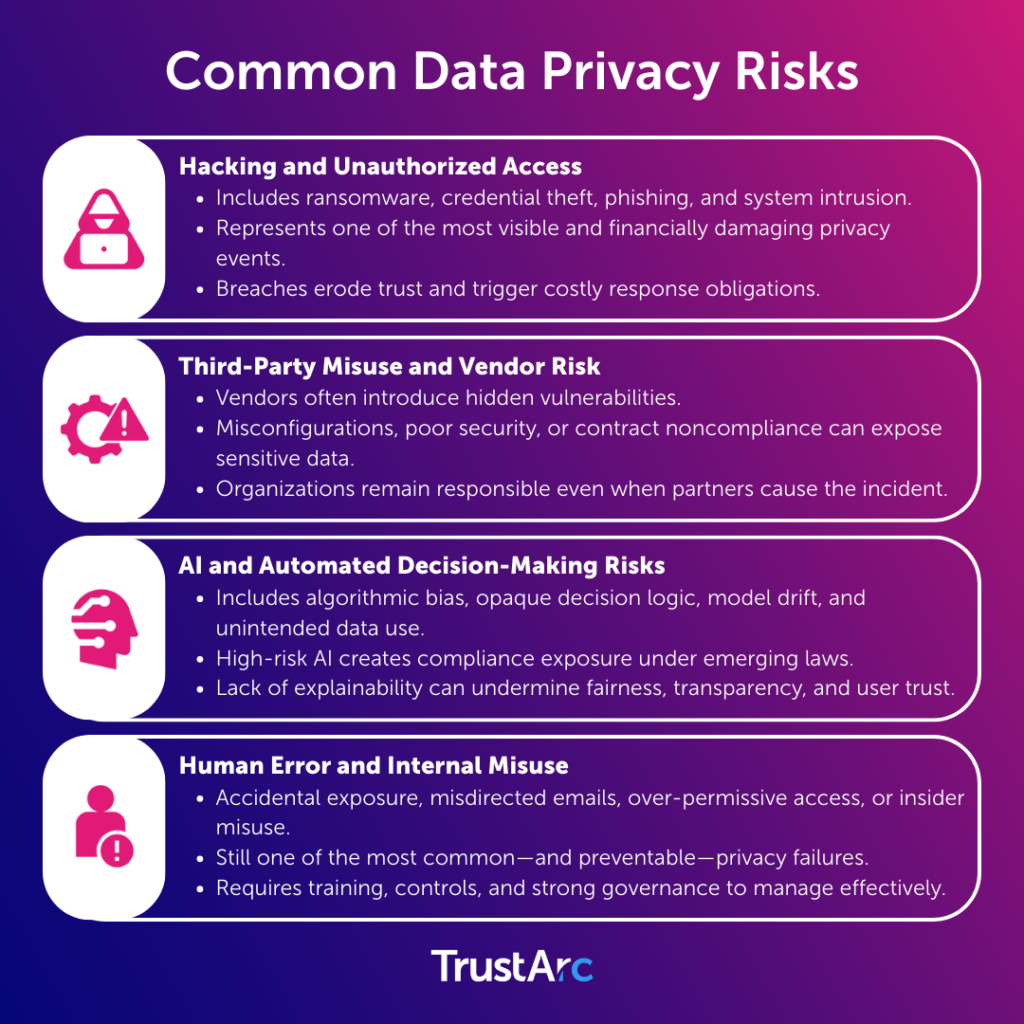
Every organization, regardless of size or industry, faces these core risks:
Unauthorized access and data breaches
A single data breach can undo years of trust building. Even when mitigated quickly, the reputation fallout can linger.
Inadequate third-party controls
One weak vendor can compromise your entire ecosystem, particularly in SaaS chains or AI supply chains.
Poor data minimization and storage practices
The longer data sits, the riskier it becomes. Data minimization isn’t a recommendation; it’s a survival tactic.
Emerging AI-related privacy risks
Algorithmic bias, opaque decision-making, excessive data collection, unpredictable output, and training on personal data all create new challenges and draw increasing regulatory scrutiny.
Human error and internal misuse
Whether accidental or intentional, employees remain one of the highest-risk areas.
Each risk isn’t just a compliance failure; it’s a trust failure.
Benefits of adopting a risk-based approach to privacy
Stronger privacy posture
A risk-based approach transforms privacy from static documentation into a living, adaptive discipline. Organizations that prioritize risks over requirements close gaps faster because they understand why those gaps matter, not just which laws mention them. This mindset produces cleaner data ecosystems, sharper internal controls, and stronger decision-making frameworks. It also helps privacy leaders anticipate issues before they escalate, shifting the program from “audit-ready” to “future-ready.” Think of it as moving from playing defense to running the whole field.
Better cross-functional alignment
Risk scoring acts as a universal translator inside the enterprise. Security teams speak in threat vectors. Engineering speaks in systems and dependencies. Product teams speak in user experience. Legal speaks in obligations and exposure. But risk? Risk is everyone’s language.
Risk is everyone’s language.
By quantifying privacy risks, leaders give every team a clear, shared understanding of priorities, reducing friction, preventing misalignment, and eliminating the lost time that plagues checklist-style programs. It creates a decision-making rhythm where each function understands its role in protecting data, enabling smoother collaboration and faster execution.
Reduced legal and financial exposure
If regulators have a “greatest hits” list of enforcement priorities—data minimization, transparency, security controls, vendor oversight—risk-based programs hit them every time. That’s because a risk-based model tackles the root causes of noncompliance: unmanaged data, unclear ownership, inconsistent processes, and high-risk automation.
By resolving these issues proactively, organizations dramatically reduce the likelihood of fines, breach expenses, litigation, and the operational chaos that comes with regulatory surprise. It’s not just about avoiding penalties; it’s about building a program that stands up to scrutiny with confidence and clarity.
Scalable, future-ready compliance
With global privacy laws multiplying faster than new characters in a Star Wars spin-off, scalability is nonnegotiable. A checklist-based program collapses under that weight. But a risk-driven program thrives because it’s built on durable principles: accountability, transparency, minimization, governance, and continuous monitoring.
When new laws emerge, organizations don’t scramble. They map new requirements onto existing risk controls. Processes flex but don’t fracture. Privacy teams avoid burnout, legal teams avoid rework, and business leaders get a model that scales seamlessly across jurisdictions, systems, and technologies.
Increased customer and regulator trust
Trust is the ultimate KPI, and a risk-based program is built to generate it. Customers reward companies that demonstrate care, responsibility, and transparency. Regulators view risk-based programs as credible evidence of accountability. Investors see them as indicators of operational maturity.
And internally? A strong risk posture boosts leadership confidence in innovation. Product teams move faster because they know the guardrails are sound. Sales teams convert faster because customers feel safe. The organization becomes known not only for protecting data, but also for protecting people.
Trust is earned through consistency, and risk-based privacy programs deliver exactly that.
Building a risk-based privacy program
A risk-based model doesn’t happen by accident. It happens through deliberate design.
Step 1: Map data flows
Understand what personal data you collect, where it lives, how it moves, and who touches it.
Step 2: Conduct ongoing risk assessments
Assess not only new systems, but existing processes, vendors, and AI models.
Step 3: Implement mitigation controls
Encryption, minimization, access limits, training, vendor clauses, secure configurations, data retention, and more.
Step 4: Monitor, audit, and improve
Regulations change. Risks evolve. Your program should too.
Step 5: Incorporate privacy-by-design
Make privacy a default, not a decision.
Step 6: Train staff and define ownership
When everyone owns a slice of privacy, the organization becomes safer and smarter.
Why checklist compliance is no longer enough
Checklist compliance creates fragile programs that break under pressure. Today’s environment demands more because:
- Global laws evolve rapidly
- Enforcement is increasing
- Data ecosystems are decentralized
- Consumers expect transparency
- AI systems introduce new, unpredictable risks
Static checklists can’t capture context-specific risks, including issues arising from training data in AI systems, high-risk vendors, or new data combinations that create unintended consequences.
Combining compliance and risk management for better outcomes
Compliance is your foundation. Risk management is your strategy.
How both approaches work together
- Compliance ensures you meet the rules.
- Risk management ensures you exceed expectations.
- Together, they form a privacy program that is defensible, scalable, and trusted.
Leaders who embrace both create programs that not only withstand regulatory scrutiny but also give the organization confidence to innovate without hesitation.
The future of privacy programs: Risk-centric and adaptive
The next generation of privacy programs won’t be built on static requirements or reactive checklists; they will be engineered for constant change. As AI accelerates the speed, scale, and complexity of data use, privacy is moving into a new era where governance, ethics, and risk oversight converge.
AI compliance, bias mitigation, transparency, explainability, and human oversight will sit at the center of privacy operations, reshaping everything from product development to vendor management. At the same time, global regulators are steadily aligning around accountability frameworks rather than prescriptive rulebooks, reinforcing the need for organizations to prove they understand and can mitigate their risks, not just document their intentions.
To keep pace, automation will become a force multiplier. AI-assisted assessments, automated data mapping, real-time risk scoring, and continuous monitoring will underpin mature programs, which, ironically, make AI essential to managing AI. As expectations rise, demonstrable accountability will carry more weight than any policy. Boards will demand clearer metrics. Regulators will scrutinize control effectiveness rather than paper compliance. Customers will favor companies that can show, not merely claim, that their practices are responsible.
Privacy leaders who embrace this evolution now will shape the standards the rest of the industry follows. They’ll build adaptive, risk-centric ecosystems designed to withstand disruption, support innovation, and earn trust in a world where transparency isn’t optional, it’s the baseline for doing business.
The strategic advantage of a risk-centric privacy program
Checkbox compliance will always have its place, but it functions as a maintenance strategy that keeps the lights on rather than driving transformation. Risk-based privacy management, by contrast, is a leadership strategy. It equips organizations to anticipate issues before they escalate, adapt quickly as laws evolve, and demonstrate the kind of accountability regulators and customers expect.
When privacy teams operate with a risk-first mindset, they gain influence across the business. They guide product decisions, strengthen security partnerships, and earn executive trust by offering clear prioritization grounded in evidence, rather than relying on checklists. This approach doesn’t just reduce exposure; it builds resilience and reinforces brand integrity in a world where trust can evaporate overnight.
Organizations that adopt risk-based governance now will be well-positioned to innovate with confidence, scale responsibly, and differentiate themselves in an increasingly data-driven market. In the new era of privacy, leadership belongs to those who manage risk, not those who merely manage requirements.
FAQs on privacy risk management
What is the difference between privacy risk management and checkbox compliance?
Risk management is proactive, strategic, and integrated. Checkbox compliance is reactive, minimalistic, and rigid.
Why is privacy risk management important for organizations today?
Because global regulations, AI systems, and complex data ecosystems require continuous evaluation—not a one-time checklist.
How does the risk assessment process help manage data privacy risks?
It identifies gaps, prioritizes mitigation, informs governance, and uncovers risks that policies alone can’t catch.
What are the most common data privacy risks businesses face?
Unauthorized access, vendor weaknesses, poor data retention, human error, and AI-driven risks such as bias or opaque decision-making.
How can companies build a strong, risk-based privacy program?
Map data flows, conduct regular risk assessments, implement controls, train teams, operationalize privacy by design, and continuously improve.
Clarity in Your Data. Confidence in Your Risks.
Map your data, uncover risks, and stay ahead of compliance with automated insights built for scale.
Map your risksCentralized Controls. Simplified Compliance.
Manage requirements, controls, and evidence in one hub for clearer, faster compliance.
Streamline privacy operations







