Today’s organizations need to proactively manage privacy risk before a crisis occurs. Just like you wouldn’t wait until after a vehicular accident to put on a seatbelt. You want to be ready.
Managing privacy risk in a rapidly changing digital world is no easy feat. In addition to consumer expectations, numerous global regulations apply to data privacy and security. Let’s also not forget that more employees are working remotely than ever.
If you haven’t already, now is the time to ramp up your privacy program to encompass risk management and data processing management activities.
As of May 2022, 71% of countries have put legislation into place to secure data and privacy protection.
Start Managing Privacy Risk
You can’t manage privacy risk if you don’t have a clear picture of your data activities. When setting up a privacy program, every organization needs to ask:
- Where is my data? What is stored? How is it used?
- What risk level is there for each of my data activities?
- What controls and assessments must be implemented to mitigate that risk?
Customer information isn’t the only type of data you need to consider. Organizations also have intellectual property data, financial data, and employee data to manage and protect securely.
The rise of a remote or hybrid workforce has also added to the heightened threat environment organizations are experiencing today. And that’s not likely to change soon.
Microsoft’s Work Trend Index found that 66% of employers around the world are making changes to accommodate hybrid work arrangements.
Even though remote and hybrid work comes with many benefits including productivity and employee retention, it puts greater pressure on privacy and security professionals to proactively manage privacy risk.
Employees are Your Greatest Vulnerability
Stanford research confirms, 85 percent of data breaches are caused by human error. Employees are both your weakest link and your strongest link when it comes to managing privacy risks.
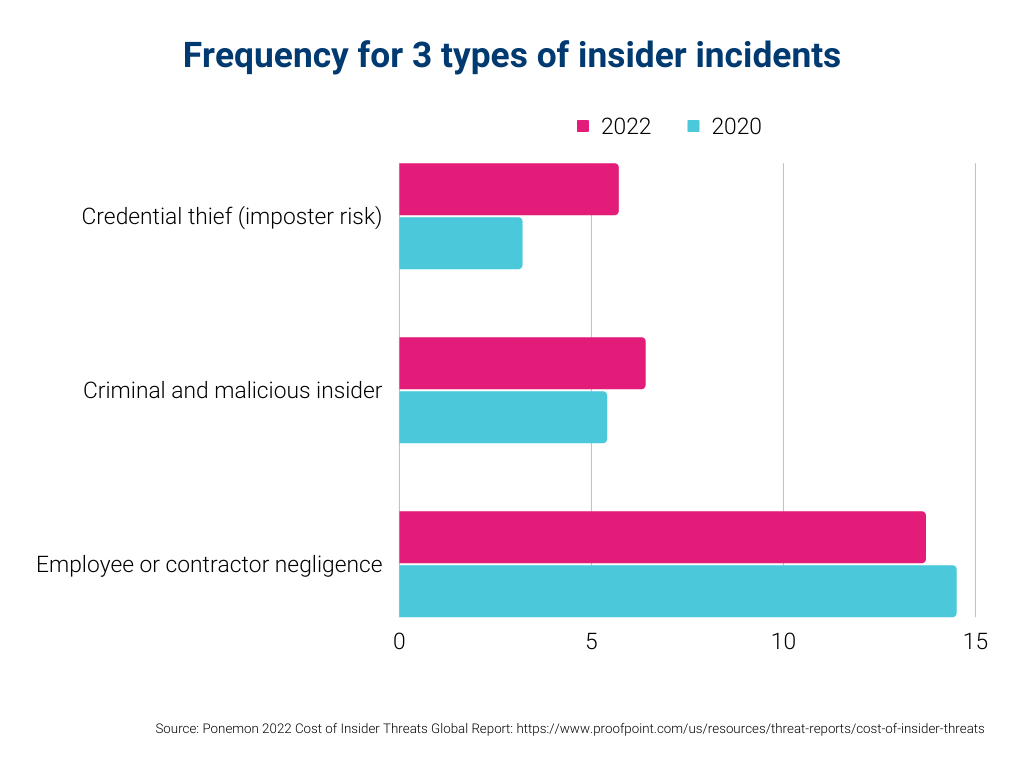
To better understand inside threats, the 2022 Ponemon Cost of Insider Global Threats Report divides insider threats into three categories.
- Employee or contractor negligence
- Criminal or malicious insider
- Credential thief (imposter risk)
Employee or contractor negligence is the greatest threat, accounting for 56 percent of insider attacks analyzed in 2022.
While technical security solutions exist, organizations can do more to protect sensitive data and manage privacy risk internally.
Privacy and security training isn’t just for a select few employees. It needs to be embedded into company onboarding, training, and consistently refreshed.
Provide employees with training that raises awareness of the importance of data protection and the consequences of a breach. Don’t forget to include how to handle attacks, company processes, and examples of insider attacks.
In addition to training, it’s important to consider what roles need access to sensitive information. Based on job scope, organizations should limit employee access to sensitive data and customer information.
Even if you think your organization is too small to be at risk, think again.
As society becomes more dependent on digital technologies, companies of all sizes will need to think proactively about data protection.
Additional Guidance to Manage Privacy Risk
HBR author, Andrew Burt, offers three strategies for organizations to manage security and privacy risk.
- Evaluate your current level of security and processes for preventing privacy and security vulnerabilities. Include the amount of time devoted to testing and maintaining software for risks. By doing so, you can determine the amount of time and effort required to adequately secure systems.
- Embed security into software design and deployment life cycle. Demonstrating that security and privacy controls are not simply an afterthought but are a core requirement in and of themselves.
- Ensure that their privacy and security controls are proportional to the volume and complexity of the code they seek to protect.
Additionally, it’s important to consider the following for managing privacy risks.
Individual Data Processing Risks
The main organizational risks from a privacy perspective are; data security, changing legal frameworks, international data flows, and enforcement action and court cases.
For individuals, privacy risks are centered on data processing sensitivity, such as the volume of data being processed and shared, the individuals involved in data processing, unnecessary data processing, and unexpected secondary data uses.
Manage Privacy Risk in Today’s Climate
With the global pandemic of COVID-19 working from home is now subjected to risk management. Data usage, transfers, and even video-conferencing can be subject to regulations.
How data privacy is maintained within a home environment such as how printed documents are handled, computer devices used while working, and data storage and clearing are additional risks that need to be considered.
Focusing Resources on High Risk Areas
Organizations need to understand the balance between risk, severe consequences of that risk, and the likelihood of that risk occurring.
To prioritize resources effectively, identify the highest risk areas and tackle those immediately. Risks with high severity and high likelihood of occurring should be prioritized for prevention, protection, and recovery measures.
Risk Reporting to Executives
The Board of Directors is responsible for risk oversight and governance – critical to organizational strategy. Key areas of risk for the board of directors include:
- Governance Risks
- Business Management Risks
- Critical Enterprise Risks
- Emerging Risks
- Board Approval Risks
Specific privacy topics reported to the board of directors and management include:
- Data breaches
- Status of compliance with GDPR
- Privacy program key performance indicators
- Progress on privacy initiatives
- Privacy litigations
Accountability is also important to report. As it demonstrates compliance, a structured review process, and detailed management reporting.
Manage, Automate, and Continuously Monitor Privacy Risk
Organizations can manage privacy risk by dividing it into five key pillars. Identify, Assess, Analyze, Remediate, and Ongoing Monitoring.
Wherever possible, you will want to automate these processes to streamline the user experience and best manage privacy risk.
The longer an organization has been established, the more likely it has amassed a rather large collection of data. These data graveyards have their own risks and may also be subjected to regulations.




